- communication on the internet is constructed of discrete, self-addressed, chunks of data called packets
- networking is done in layers
- Application layer (SMTP, FTP, HTTP)
- Transport Layer (port-addressed communications, TCP, UDP)
- Internet Layer (IP)
- Link Layer (Transformation of data within local network, Ethernet)
- Physical Layer (Traansmission of raw bits vover physical data link, WIFI)
TCP
- breaks messages into segments
- delivers packets reliably and in order
- routers forward packets towards destination
- ports identify connection along with IP addresses
IP Packet Fragmentation
- sender writes unique value in identification field of packet
- if router fragments packet, then it copies the
idinto each fragment - eaach fragment retains the same
idfield value from the original packet offsetfield indicates position of frgment in bytesMoreFragmentsflag to tell that the fragment is not the last oneDontFragmenttells gateway not to fragment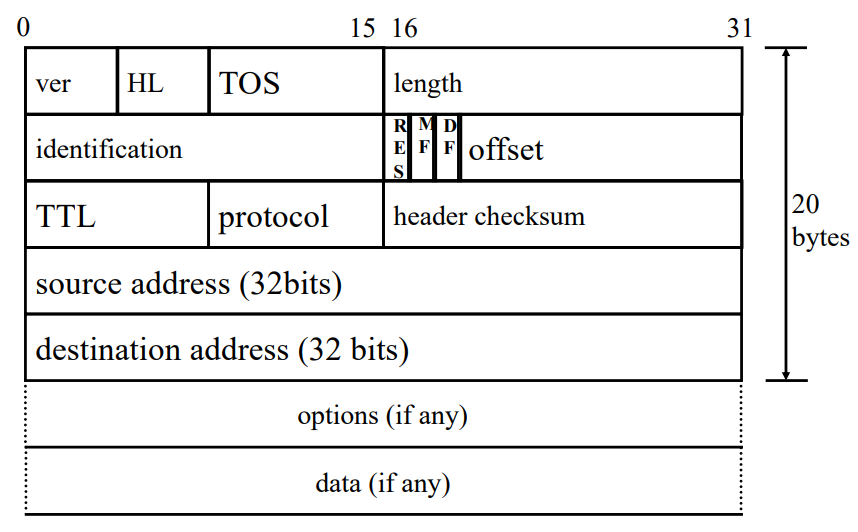
Example:
Given fragment
S [ len=4000 | id=x | MF=0 | offset=0 ] ->
A [ len=1500 | id=x | MF=1 | offset=0 ] +
B [ len=1500 | id=x | MF=1 | offset=1480 ] +
C [ len=1040 | id=x | MF=0 | offset=2960 ] +Where the offset of the first fragment is decremented by 20 bytes, for the header part of the IP packet (see above)
TTL (Time-To-Live)
- designed to limit packet looping around in a network forever
- each router decrements the TTL field
- if
TTL == 0, then router discards packet
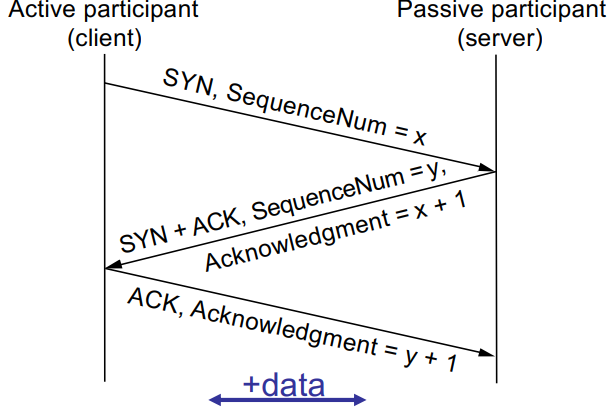
TCP Primer
- stateful bidrectional session between two
IP:portendpoints - each side maintains:
- Sequence Number: sequence base (start from here) + count of bytes sent
- Acknowledgement Number: ack base + count of bytes received
- Special packet flags:
- SYN: I want to start a connection
- FIN: I want to shut down a connection
- RST: We are killing this connection
- The flags do this:
TCP/IP Security
1970s
- End-to-End Principle (focuses on transmission of data between endpoints)
- network is simple, efficient, scalable
- Robustness: when sending, the system should strictly follow protocol for data, but when recieving data, should tolerate minor errors
Built-in Assumptions
- TCP/IP should only be ued an intended
- correct packet headers
- consideration of others’ resources
- hosts controlled by trusted administrators
- random people cannot get on the nwtwork
- correct information needs to be reported by hosts
- protocols should be implemented correctly
1980s
- not everyone can be trusted
- threat model changed to :
- cannot trust everyone (some hosts are compromised)
- untrusted insiders on internal networks
- anyone can connect to a public network
- networks generally still trusted
Today
- these no longer work today
- the network is very open, where anyone can get on it (including bad people)
- attackers can immediately and intentionally misuse protocols/resources
- not all devices are trustworthy
Attacker Models
- person in the middle, eavesdropping, off-path (inject traffic into network)
- many layers to view your own packets
- network (routers, switches, access points)
- unprotected WIFI network
- non-switched Ethernet: everyone on same network
- switched Ethernet: everyone gets their own link, but sometimes someoen can intercept your traffic
- No authentication in TCP/IP
- attacker can spoof your IP
- Attackers can blast packets at a target with a spoofed address and make it look like someone else is attacking them.
IP Routing
Given IP 8.8.8.8
- Check if host is on local → send directly
- If not, → default gateway
- Create IP packet
- Create and send link layer (i.e. Ethernet) frame
- 48 bit source addr, 48 bit destination addr
[ dest MAC addr | src MAC addr | ethertype | <-- data --> | crc checksum ]
Address Resolution Protocol
- maps IP to MAC within a LAN (local area network)
- used to find the MAC corresponding with the IP addr
- ARP Request (Broadcast)
- A wants to send to B, where B has addr
141.23.56.23 - A does not know B’s address
- A sends request, asking, who is
141.23.56.23 - ARP request is broadcasted across all devices on network with MAC addr
0xFFFFFFFFFF
- A wants to send to B, where B has addr
- ARP Reply (Unicast)
- Each device on LAN checks if the IP addr matches its own
- Only B responds, sending an ARP reply back to A with its MAC addr
- This is unicast, sent by one person directly to A
ARP Spoofing
- ARP is broadcast on a local subnet, so anyone can pretend to be someone else
- Attacker can impersonate any other host
- mitigate with static ARP tables (impractical, but better for small, fixed networks)
- Port Binding: restrict MAC/IP on single port at a time
- depend on higher level host auth to save you (SSH/TLS)
IP Spoofing Attacks
- no auth in Link or Internet layers
- even if routing is correct, Eve can still spoof Alice’s IP adr
- recall Eve is enemy
- UDP is trivial, each data is independent of others
- TCP: complicated, but possible
- need to guess Bob’s SYN-ACK number
Blind Port Scanning
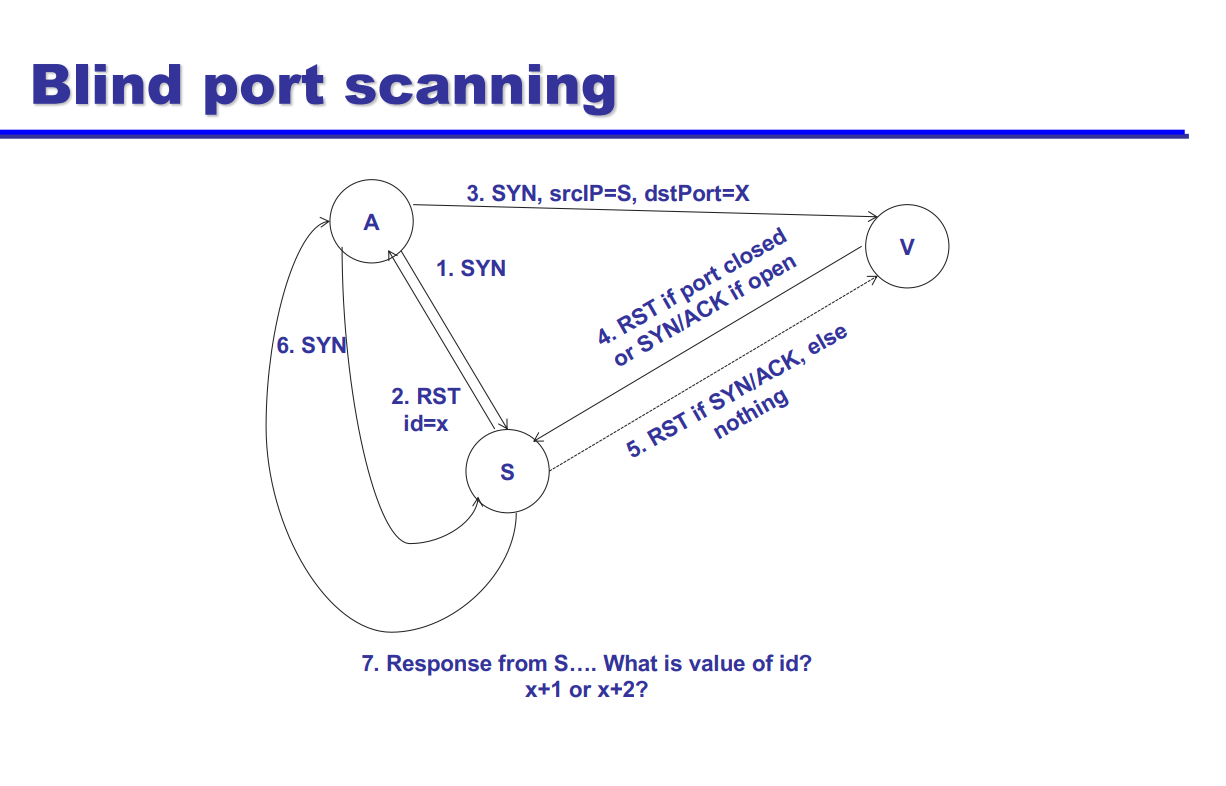
- used to determine if a specific port on a target system denoted as V is open or closed without recieving direct responses from the target
- can by pass firewalls and what not using an intermediate S that interacts with both attacker A and victim V
- A sends SYN to S
- S sends RST to A, with
id=x - A sends SYN to V with
id=x, pretending to be S - V processes SYN and has two options:
- Open: V sends SYN-ACK to S
- Closed: V sends RST to S
- V will:
- If V sends SYN-ACK, S responds with RST to terminate
- If V sends RST, S does nothing
- S responds with RST, revealing value of
x- If
id=x+2, then S sent an RST to V, meaning the port was open - If
id=x+1, then the port was closed
- If